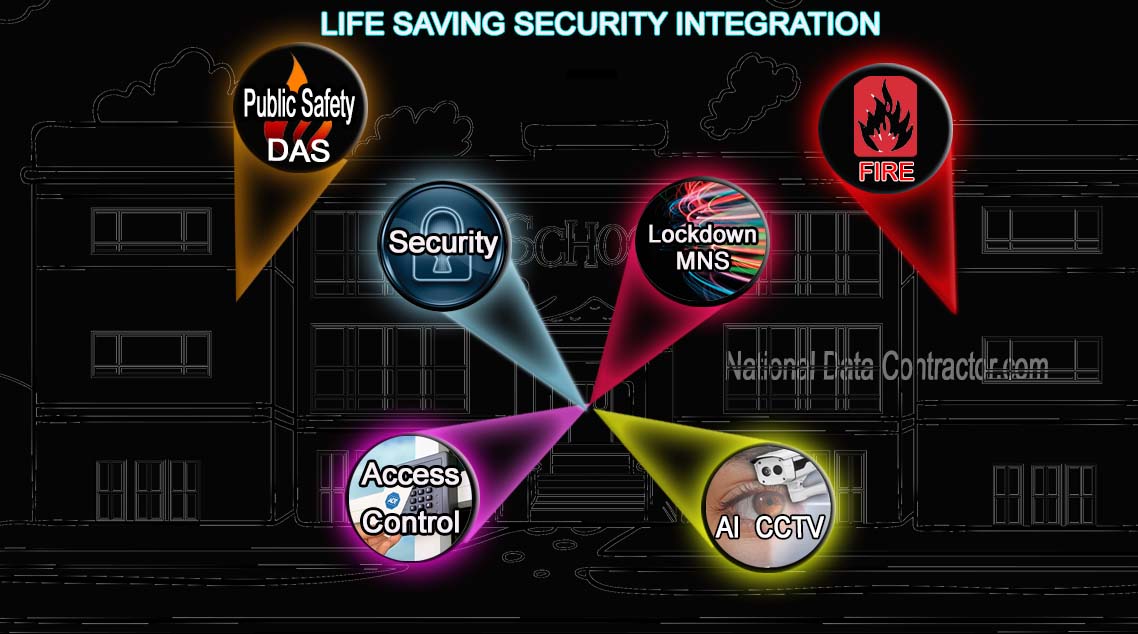
How to Build a Security System to Protect Your Life: Integrating Access Control, CCTV, AI, and Alarm System for Comprehensive Safety.
Security is paramount to any business, as such, the demand is growing by the day. Businesses and organizations are increasingly turning to advanced technological solutions to safeguard their assets, data, and personnel. Among the myriad of tools available, access control systems stand out as a much needed security strategy. From restricting unauthorized entry to monitoring and managing user activities, these systems offer a multifaceted approach to protecting physical and digital environments.
Understanding Access Control Security
Access control security refers to the practice of regulating and monitoring entry to physical spaces, digital networks, and sensitive information. It involves the implementation of mechanisms that authenticate, authorize, and track individuals' access rights. By enforcing strict access policies, organizations can mitigate risks associated with unauthorized intrusion, theft, and data breaches.
Types of Access Control Systems
Access control systems come in various forms, each tailored to address specific security needs and environments. Here are the primary types that we encounter:
-
Discretionary Access Control (DAC): DAC grants users control over the resources they own, allowing them to determine who can access them and the level of access granted. While flexible, DAC relies heavily on user discretion, which can lead to inconsistencies in security enforcement.
-
Mandatory Access Control (MAC): In MAC systems, access decisions are centrally administered based on predefined security policies. Users have limited control over access permissions, as they are determined by system administrators. This approach is commonly used in environments where data confidentiality is paramount, such as government and military settings.
-
Role-Based Access Control (RBAC): RBAC assigns access rights to users based on their roles within an organization. By grouping users into roles and defining the privileges associated with each role, RBAC simplifies access management and ensures consistency across user permissions.
-
Attribute-Based Access Control (ABAC): ABAC evaluates a set of attributes associated with users, resources, and environmental conditions to make access decisions dynamically. This granular approach enables organizations to implement finely detailed access control plans based on contextual factors such as time, location, and device characteristics.
-
Biometric Access Control: Biometric access control systems utilize unique physiological or behavioral traits, such as fingerprints, iris patterns, or facial features, to authenticate users. By eliminating the need for traditional authentication methods like keys or passwords, biometric systems offer enhanced security and convenience.
Applications of Access Control Systems
Access control systems find applications across various sectors, providing highly customized solutions to diverse security challenges. Some common use cases include:
-
Physical Security: Access control systems secure physical spaces such as office buildings, warehouses, and manufacturing facilities by restricting entry through keycards, biometric scanners, or electronic locks. These systems help prevent unauthorized access, theft, and vandalism while maintaining a detailed log of entry and exit activities.
-
Information Security: In digital environments, access control systems safeguard sensitive data and resources from unauthorized access or manipulation. By enforcing authentication mechanisms and encryption protocols, these systems protect against cyber threats such as data breaches, malware attacks, and insider threats.
-
Time and Attendance Management: Access control systems can also streamline time and attendance tracking by recording employees' entry and exit times automatically. Integrated with payroll systems, these solutions facilitate accurate attendance management and payroll processing while deterring time theft and unauthorized overtime.
-
Visitor Management: For facilities welcoming guests, access control systems offer efficient visitor management solutions. By issuing temporary access credentials or QR codes, organizations can monitor and regulate visitor entry while ensuring a seamless guest experience.
That summarizes the basics of access control systems. Now, let's look at how access control has emerged as a pivotal component in integrating with other systems to further heighten security measures.
In recent years, educational institutions have faced heightened security concerns, particularly regarding active shooter situations. To address these threats, many schools and universities have turned to access control systems, coupled with mass notification and alarm systems, to enhance safety protocols. These system generally then become known as School shooter lockdown systems.
Deployment in Educational Institutes:
Access control systems in educational settings serve a dual purpose: regulating entry to facilities and enabling swift lockdown procedures during emergencies. These systems typically include:
-
Physical Access Control: By employing keycards, biometric readers, or electronic locks, educational institutions can control access to buildings, classrooms, and sensitive areas. Restricting unauthorized entry helps prevent potential threats from gaining access to campus premises, and allowing entry granted to first responders further warrants the use of these systems.
-
Mass Notification Systems: Integrated with access control, mass notification systems enable administrators to disseminate critical alerts and instructions to students, faculty, and staff in real-time. In the event of an emergency, such as an active shooter situation, automated alerts can be broadcasted via text messages, emails, loudspeakers, or via tv monitors, thus ensuring swift communication and coordinated response efforts.
Integration with Alarm Systems:
In addition to access control and mass notification systems, educational institutes often integrate these technologies with alarm systems for comprehensive security coverage. Alarm systems serve as early warning mechanisms, detecting unauthorized entry, suspicious activities, or potential threats and triggering immediate responses. Integration with access control allows for automated lockdown procedures, wherein doors are secured, and access is restricted to authorized personnel only.
Benefits of Integration:
-
Rapid Response: By automating lockdown procedures through integration with access control, educational institutes can initiate swift responses to potential threats, minimizing the risk of harm to students and staff.
-
Enhanced Communication: Mass notification systems enable rapid communication during emergencies, ensuring that critical information reaches all need to be reached parties promptly and accurately.
-
Centralized Management: Integrating access control, mass notification, and alarm systems under a centralized management platform streamlines security operations, allowing administrators to monitor and control multiple systems from a single interface.
-
Deterrence and Prevention: Visible presence of access control and alarm systems serves as a deterrent to potential threats, while proactive measures such as restricted access help prevent unauthorized entry and mitigate risks.
Integrating CCTV Cameras to Strengthen Access Control Systems
In the realm of security integration, Closed-Circuit Television (CCTV) cameras play a crucial role in enhancing the effectiveness of access control systems. By combining CCTV surveillance with access control measures, notification systems, and alarms, organizations can achieve comprehensive security coverage and bolster their ability to prevent and respond to security incidents.
Benefits of Integrating CCTV Cameras:
-
Enhanced Monitoring: CCTV cameras provide real-time visual monitoring of entry points, corridors, and other critical areas, allowing security personnel to visually verify individuals' identities before granting access. This visual confirmation adds an extra layer of security, especially in high-risk environments.
-
Event Verification: In the event of unauthorized access attempts or security breaches, CCTV footage serves as valuable evidence for post-incident analysis and investigation. By capturing detailed visuals of incidents, organizations can identify intruders, assess the extent of the breach, and take appropriate remedial actions.
-
Behavioral Analysis: CCTV cameras enable security personnel to observe individuals' behavior patterns and detect suspicious activities in real-time. By integrating video analytics and motion detection algorithms, organizations can automate alerts for unusual behaviors, such as loitering or unauthorized access attempts, enhancing proactive threat detection capabilities.
-
Incident Response: In conjunction with access control and alarm systems, CCTV cameras facilitate coordinated incident response efforts. When triggered by access control events or alarm activations, CCTV cameras can automatically pan, tilt, and zoom to the affected areas, providing live visuals to security personnel and first responders for timely intervention.
Integration with Access Control and Alarm Systems:
-
Event-driven Recording: CCTV cameras can be integrated with access control and alarm systems to enable event-driven recording. When access control events or alarm triggers occur, CCTV cameras automatically start recording footage, providing synchronized visual documentation of security incidents for subsequent review and analysis.
-
Remote Monitoring and Management: Integrated CCTV systems allow security personnel to remotely monitor access control events and alarm activations from a centralized management platform. Real-time access to CCTV footage enables rapid assessment of security threats and facilitates informed decision-making for effective incident response.
-
Automated Alerts and Notifications: By integrating CCTV cameras with access control and alarm systems, organizations can configure automated alerts and notifications for specific security events. For example, security personnel can receive instant alerts when unauthorized access attempts are detected, enabling prompt intervention to prevent potential security breaches.
Integration of Paging System:
Incorporating a paging system into access control, CCTV, AI, and alarm systems enhances communication during emergencies. By broadcasting critical alerts and instructions across various channels like PA speakers, text messages, or digital displays, organizations can ensure rapid and effective communication to all stakeholders. This integration facilitates a coordinated response, assists in guiding individuals to safety, and helps in managing evacuation procedures efficiently. By connecting paging systems with existing security infrastructure, businesses can strengthen their overall security system and improve emergency preparedness.